Bybit Hackers Return to Launder Stolen Funds, FBI Steps Up Surveillance

Jakarta, Pintu News – The hackers responsible for the attack on cryptocurrency platform Bybit are at it again. According to recent reports, the group has moved around 62,000 Ethereum worth Rp2.28 trillion ($138 million) as part of their efforts to cash out stolen funds.
Although this activity had previously slowed down due to warnings from the FBI, hackers seem to be active again and continue to shift their assets to various platforms.
Lazarus Hackers Have Laundered 68% of Stolen Funds

The Lazarus group, which has been linked to the IDR 23.1 trillion ($1.4 billion) attack on Bybit on February 21, 2025, now only has around 156,500 ETH left to move. An anonymous analyst revealed that to date, the group has managed to move a total of 343,000 ETH out of the total 499,000 ETH they stole from the platform.
In the progression, the amount of Ethereum that has been laundered increased from 54% on February 28 to 68% currently. It is expected that in the next few days, the remaining stolen funds will continue to be moved to various platforms to eliminate traces of the transaction.
Also Read: The Future of Pi Coin (PI) in the Cryptocurrency World: Will PI Capi $5? Here’s the Technical Analysis!
FBI and Blockchain Platforms Seek to Hinder Fund Laundering
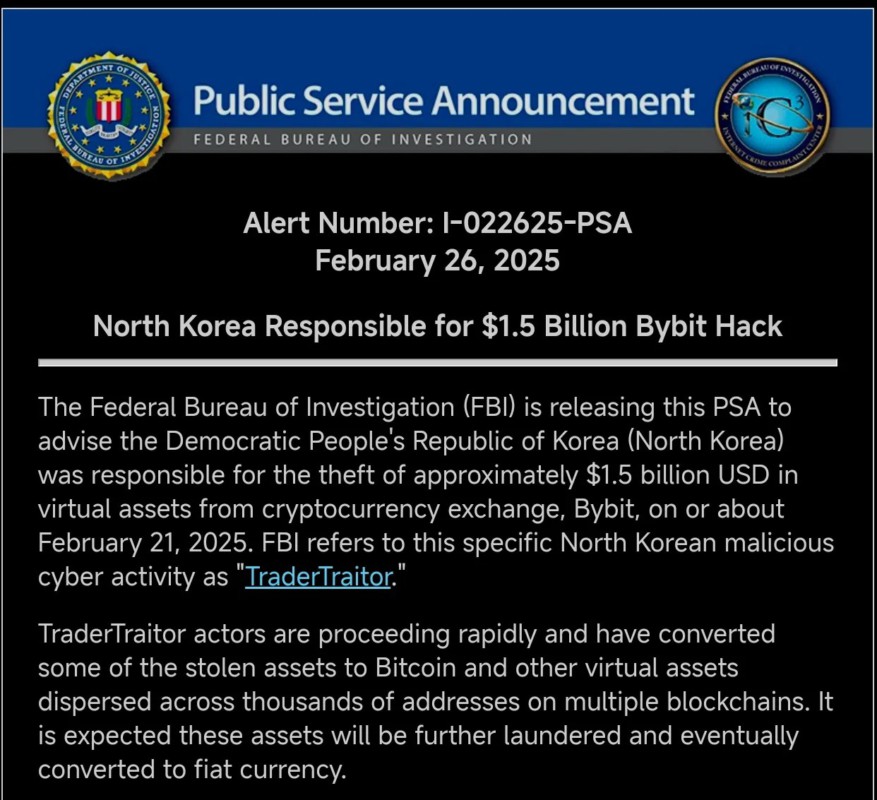
The group’s fund laundering activities had previously slowed down after the FBI issued a warning to node operators, crypto exchanges, and other financial platforms to block transactions affiliated with the hackers. The FBI also confirmed that the group involved in this attack has ties to North Korea and is known by various names, including Lazarus Group, APT38, BlueNoroff, and Stardust Chollima.
To help identify illegal transactions, the FBI has shared a list of 51 Ethereum addresses associated with the Bybit hackers. Meanwhile, blockchain analysis company Elliptic has also flagged more than 11,000 crypto wallet addresses allegedly used by this group to launder their stolen funds. With its rapid detection system, Elliptic was able to identify the relevant addresses within just 30 minutes of the announcement of the hack, helping to prevent more funds from being laundered undetected.
Hackers Use Advanced Techniques to Cover Their Tracks
According to blockchain forensics firm Chainalysis, the hackers used various methods to hide their activities. Some of the stolen ETH was converted into Bitcoin , DAI (stablecoin), and other cryptocurrencies. The funds were then moved through decentralized exchanges (DEXs), cross-chain bridges, and instant exchange services that did not implement Know Your Customer (KYC) procedures.
One of the platforms allegedly used by Lazarus Group to launder funds is the THORChain cross-chain asset exchange protocol. This sparked outrage from the crypto community, who demanded action against the transactions made by the hackers. As a result, the platform held a vote to determine whether they should cancel all transactions related to the hacker group.
This situation also caused internal turmoil at THORChain. One of their lead developers, Pluto, decided to resign from the project, while a validator also threatened to leave the platform. THORChain’s founder, John Paul Thorbjornsen, stated that he is no longer involved with the protocol’s operations and confirmed that no FBI or Office of Foreign Assets Control (OFAC) blacklisted wallets interact with THORChain.
Bybit Hack: One of the Biggest Hacks in Crypto History
The attack on Bybit became one of the biggest hacks in the history of the cryptocurrency industry. With total losses reaching Rp23.1 trillion ($1.4 billion), this incident surpassed even the Ronin Bridge hack in March 2023 that caused losses of Rp10.7 trillion ($650 million).
Although various measures have been taken by authorities and blockchain platforms to stop the laundering of these funds, hackers still seem to have loopholes to move their funds. Therefore, the crypto community, regulators, and blockchain service providers need to continue to increase surveillance to prevent similar activities in the future.
Also Read: Pi Network Price Plunges 18% After Legal Warning from Vietnam (3/2/25)
That’s the latest information about crypto news today. Get more information about crypto academy from beginner to expert level only at Pintu Academy and enrich your knowledge about the world of crypto and blockchain.
Follow us on Google News to get the latest information about crypto and blockchain technology. Enjoy an easy and secure crypto trading experience by downloading Pintu Crypto via Google Play Store or App Store now.
Experience web trading with advanced trading tools such as pro charting, various order types, and portfolio tracker only at Pintu Pro. Click Register Pintu if you don’t have an account or click Login Pintu if you are already registered.
*Disclaimer
This content aims to enrich readers’ information. Pintu collects this information from various relevant sources and is not influenced by outside parties. Note that an asset’s past performance does not determine its projected future performance. Trading crypto carries high risk and volatility, always do your own research and use cold hard cash before investing. All activities of buying andselling Bitcoin and other crypto asset investments are the responsibility of the reader.
Reference:
- Cryptopolitan. Bybit Hackers Resume Laundering, Move 62,000 ETH. Accessed March 3, 2025.
- Featured Image: The image created by AI




