Pintu Bug Bounty Program Policy
Last updated: 24 October 2024
Introduction
Pintu (hereinafter referred to as Pintu, we, our, us) is Indonesia’s leading Blockchain technology company. We are a strong Indonesian and International team passionate about using blockchain to drive positive change in Indonesia.
Here at Pintu, we take security seriously and understand the importance and value that external security researchers can bring. Thus we invite external security researchers (hereinafter referred to as the reporter, you) to report any security issues on our assets. We will investigate all the reports sent to us and seek to reward the reports that meet our reward criteria and follow our disclosure policy.
No technology is perfect and Pintu believes that working with skilled security researchers across the globe is crucial in identifying weaknesses in any technology. We look forward to receiving reports from you to keep our customers and businesses safe.
By joining, accessing, and participating in the Bug Bounty Program (“Program”), the reporter agrees to comply with and will be bound to all the policies, terms, and conditions as written in this Program Policy (“Policy”) and acknowledge that this Policy constitutes a legally binding agreement between you and Pintu. If the reporter does not agree to the Policy, the Reporter may stop accessing, participating, and/or joining the Program.
Disclosure Policy
For all the reports that are sent to us, we require the reporter to follow our following disclosure policy:
- Once a security issue has been identified the reporter is required to immediately report the issue by sending an email to [email protected]
- The details of the security issue cannot be shared with anyone without written approval from us
- While looking for security issues, the reporters must make a good-faith effort to avoid any privacy violations. The reporters have to ask us first for more information before engaging in activities that might violate our other policies.
- Found security issues are not to be exploited in any way. This includes making the issue public (without our consent) or exploiting it to make profits or cause reputation damage.
Response SLA
We will make the best effort to meet the following SLAs for researchers participating in our program:
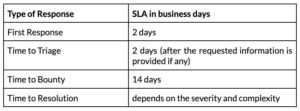
We’ll try to keep you informed about our progress throughout the process.
Actions to Avoid
The reporters are prohibited from performing the following actions:
- Testing on accounts other than those that you own
- Automated testing using tools such as scanners
- Excessive request attempts that affect the availability of our services to all users
- Destruction of data or service
- Do not copy any files from our applications/servers and disclose them
- Denial of service (DoS) attacks on applications, servers, networks or infrastructure are strictly forbidden
Reporting Criteria
- All the reports are to be reported at [email protected]
- The reporter must mention any additional information, data, and sensitive information that was accessed while identifying the issue.
- We encourage researchers to include videos or screenshots (proof-of-concept) in reporting security vulnerabilities. These files should not be shared publicly. This includes uploading to any website that is publicly accessible (like Vimeo, Imgur, etc.). If the file exceeds 50 MB, upload the file to a secure online folder such as Dropbox that is protected with a password.
- The reporter must report only one report per issue and provide any additional information and follow-up information requested by us.
Report Evaluation
To be deemed valid, a report must demonstrate a vulnerability in a service provided by Pintu that harms Pintu or Pintu customers. Reports that include a clear Proof of Concept or specific step-by-step instructions to replicate the vulnerability are considerably more effective at communicating a researcher’s findings and are therefore far more likely to be deemed valid.
To qualify for a bounty, a report must contain vulnerabilities and assets that are listed in scope. Pintu awards bounties based on the severity of the vulnerability based on two factors: Impact and Exploitability.
Impact describes the effects of successful exploitation upon Pintu systems or customers. We make this assessment primarily by examining the effects of exploitation on confidentiality, integrity, or availability of underlying information.
Vulnerabilities that require considerable response and remediation efforts or could result in reputational damage are also considered to have a greater impact.
Reward Policy
Only vulnerabilities with a working proof of concept showing how they can be exploited and vulnerabilities with a real security impact will be considered eligible for monetary rewards. Determination of whether a reported issue sufficiently meets the bar for monetary rewards is done at Pintu’s discretion.
- Pintu reserves the right to determine the bounty amount and whether a report qualifies for a reward, where such a decision by Pintu is final and cannot be contested.
- The report and identified issue must be original and we award the first reporter to report an issue. Any previously known issue will be treated as a duplicate.
- Security issues with a working proof-of-concept that demonstrates impact will be rewarded.
- We determine bounty amounts based on a variety of factors, including (but not limited to) impact, ease of exploitation, and quality of the report. Note that extremely low-risk issues may not qualify for a bounty at all.
- We seek to pay similar amounts for similar issues, but bounty amounts and qualifying issues may change with time. Past rewards do not necessarily guarantee similar results in the future.
- For any multiple findings that can be resolved in a single fix, only a single report will be eligible for a reward (e.g: same endpoint that has the same vulnerability category, same impact but in different parameters or different HTTP method, and other findings which similar to that scenario)
- Any reports considered out of scope but have a serious security impact, will be reviewed and rewarded on a case-by-case basis.
- Rewards for resurfaced bugs would be on a case-by-case basis and may not adhere to the rewards table.
- We are keen to work with the Bug Hunter to make sure that every researcher’s finding is rewarded fairly – based on the vulnerability’s impact on business and overall severity. Extraordinarily severe issues or those with extreme impact may be rewarded up to $1000.
- Pintu reserves the right not to award or cancel the rewards for the reporters if it is reasonably determined or suspected that the reporters have:
- Committed fraud or other illegal acts that violate the law; and/or
- Violated these terms and conditions under this Policy, any applicable policies during the use of Pintu platform by reporters, and/or applicable laws and regulations.
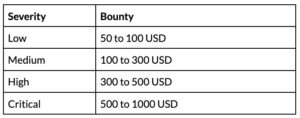
Rewards Table
The details of the rewards for reporters who meet the terms and conditions of this Policy (“Eligible Reporters“) are as follows:
For the avoidance of doubt, Pintu and the reporter shall be responsible for their own tax obligations arising from any rewards provided in this Program.
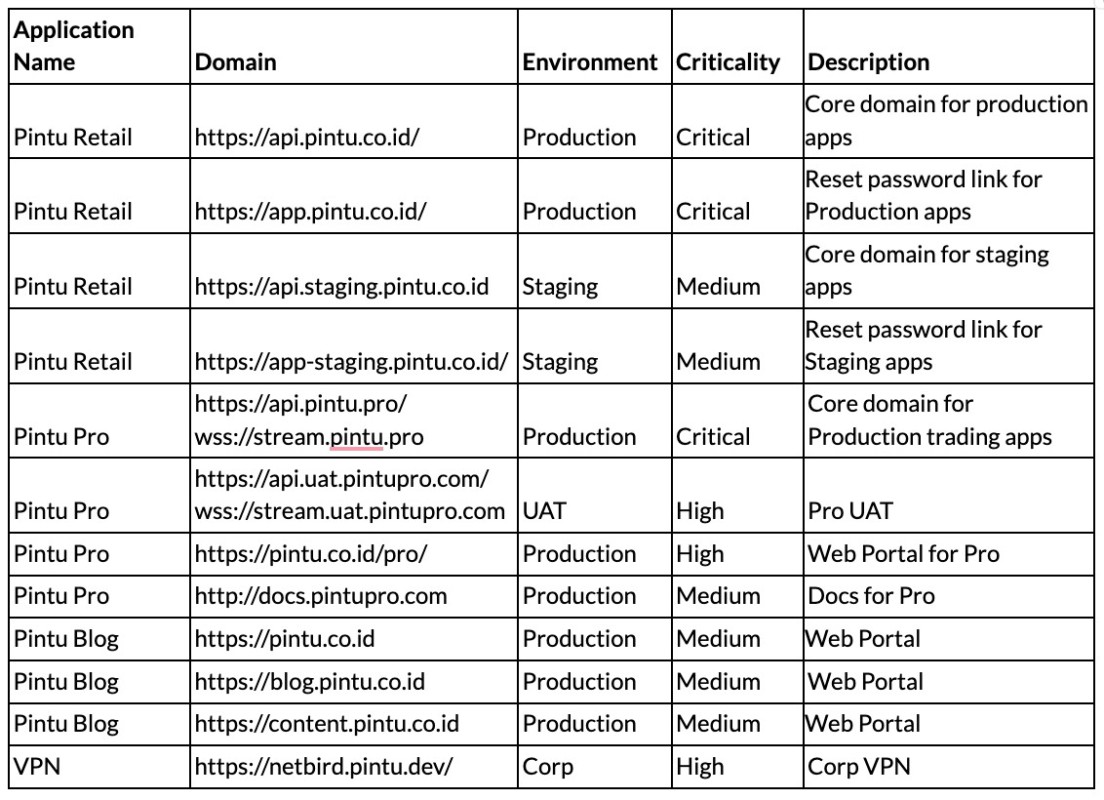
Assets in Scope
Web Assets
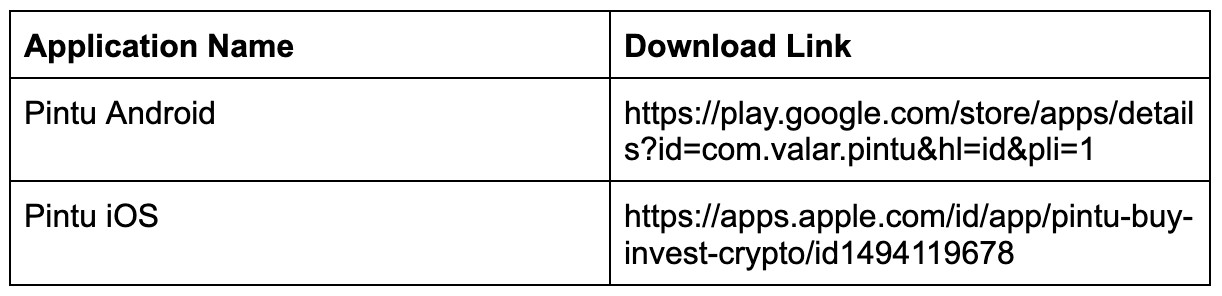
Mobile Apps
In Scope Vulnerabilities
Below are the types of submissions that are preferred to be accepted
- Broken authentication
- Multi-Factor Auth Bypass
- OTP Bypass (Untrusted Devices)
- Bypass Authorization Schema
- SQL Injection
- Reflective and Stored XSS Injection
- Sensitive Data Exposure
- Business Logic with a real security impact
- Cross-Site Request Forgery (HIGH-CRIT ACTION)
- Server-Side Request Forgery
- Remote Code Execution
- Local File Disclosure (Depending on the criticality of the File)
- Server Side Injection Templates
- Payment Manipulation
Out-of-Scope Vulnerabilities
- Any issues related to spam or that require using social engineering techniques.
- Denial-of-service and Distributed Denial-of-service related attacks
- Any issues related to content injection and “HTML injection” are out of scope unless the report can demonstrate a significant risk or impact
- Theoretical vulnerabilities without actual proof of concept
- Any issues related to crashing of the Mobile app which cannot be reproducible on the latest OS version or latest version of the Mobile app
- Issues relating to Clickjacking/UI redressing that cannot demonstrate security impact
- Email/Username enumeration
- Issues relating to Information disclosure without any security impact (Reports relating to stack traces, directory listing, path disclosure, api key, firebase token, etc.)
- Tab-nabbing
- Self-XSS and XSS require an outdated browser to exploit or significant user interaction.
- Issues that can only be exploitable on out-of-date browsers, software, or platforms
- Vulnerabilities in third-party applications that don’t impact Pintu or Pintu’s user data
- Use of known vulnerable libraries or CVE without actual proof of concept
- Lack of security flags in a cookie
- Issues related to unsafe SSL/TLS cipher suites or protocol versions
- Exposure of internal IP addresses or domains
- Missing security headers that do not lead to direct exploitation
- CSRF issues without significant security impact
- Issues that require physical access to a user’s device
- Absence of rate-limiting (or disagreement over existing thresholds)
- XSS attacks via POST requests, or self-XSS (unless you provide a PoC that shows impact on other Pintu users)
- XSS or XSRF that requires header injection
- Attacks requiring access to the network traffic (e.g. manipulation of DNS queries or responses)
- Attacks that require that the user’s device is compromised (malware, jailbreak, etc)
- Password and account recovery policies, such as reset link expiration or password complexity requirements
- Issues related to software or protocols, not under Pintu’s control
- Reports from automated tools or scans
- Any physical attempts against Pintu’s property or data centers
- Concerns related to email domain authentication (SPF, DMARC, DKIM, etc)
- Non-reproducible issues of any sort
- Any best practice recommendation without real security impact
- Public Zero-day vulnerabilities that have had an official disclosure less than 1 month before are on a case-by-case basis
- Issues relating to dangling DNS CNAME without any security impact
- Issues relating to credential breach
- Issues relating to missing DNS Record
Safe Harbour
Reporters who conduct activities in a manner that is consistent and compliant with the above policy will be considered authorized individuals or entities, Pintu will not initiate any legal action against them.
- CONFIDENTIALITY – All reported security vulnerabilities should not leak into public spaces. The reporter must obey all the confidentiality provisions as written in this Policy.
- INTEGRITY – Only report security issues deemed valid and do not use the findings of the security vulnerabilities for tampering purposes. If there is more than 1 report regarding the same security problem, the first one to report will be considered valid.
- PROFESSIONALISM – Security researchers are fully responsible for the findings reported and should be contacted if necessary for explanation or other complementary information
Payment Process
For Indonesian
The payment process may take up to 2 weeks from when Pintu decides the reporter is eligible to get the reward and will be made through Indonesian Banks.
Bank account and personal details will be requested to process the payment and legal purposes.
For Others
The payment process may take up to 1 month from when Pintu decides the reporter is eligible to get the reward and will be made through USDT over Ethereum or Polygon network.
Receiving wallet address and personal details will be requested to process the payment and legal purposes.
Terms and Conditions
By joining the program, besides all the terms and conditions as stated in the Policy above, the reporter agrees to follow the terms and conditions as follows:
- Pintu reserves the right from time to time to change, add, and/or modify the policy and its terms and conditions. If the reporter does not agree with such changes, additions, and/or modifications, they may cancel their participation in the Program. Pintu reserves the right to cancel the reward if the reporter does not comply with these or if events beyond Pintu’s control reasonably prevent Pintu from continuing the Program or providing the rewards under applicable laws.
- The reporter acknowledges and agrees that if at any time in the future they fail to comply with the Policy, Pintu’s terms and conditions, and/or Pintu’s privacy policy in the Pintu application or if Pintu suspects or determines that the reporter is involved in fraudulent or abusive activities that may harm other users, Pintu, or third parties, then Pintu, at its sole discretion, may take necessary actions including but not limited to withholding any benefits or earnings, seeking compensation, temporarily suspending, terminating access, restricting access, deleting accounts, and banning the use of any Pintu services.
- Confidentiality
- The Reporter (“Receiving Party“) will maintain confidentiality of the existence of this Agreement and all the provisions contained therein, and any information exchanged in connection with and in the implementation of its obligations under this Agreement (“Confidential Information“) and will not disclose it to others prior written consent from Pintu (“Disclosing Party”).
- The confidentiality obligations of the Receiving Party will not apply to information that is:
- constitutes or becomes part of the public domain without violating this Agreement and not through the actions or omissions of the Receiving Party or its Affiliates;
- has been independently developed by the Receiving Party or its Affiliate through the efforts of their employees or agents who do not have access to the Confidential Information;
- can be reasonably proven to have been disclosed or made available to the Receiving Party or its Affiliates not in secret by a third party who has the right to do so;
- must be disclosed by order of a court or arbitration body of competent jurisdiction; and/or
- disclosure has been approved with the prior written consent of the Disclosing Party
- The Receiving Party may not, directly or indirectly: (i) use any Confidential Information other than to exercise its rights and obligations under this Agreement; or (ii) disclose to any third party or permit any third party to have access to any Confidential Information, except as expressly permitted herein.
- In maintaining the confidentiality of Confidential Information, the Receiving Party may not use a standard of care that is less than that used by a reasonable person to maintain his own confidential information of a similar nature.
- For the avoidance of doubt, any Confidential Information exchanged between the Parties prior to signing this Agreement for the purposes of this Agreement will be treated in the same manner and will be subject to the same treatment as Confidential Information made available after the execution of this Agreement.
- The Receiving Party may disclose Confidential Information to Representatives on a need-to-know basis. The Receiving Party represents and warrants that it will make and ensure its Representatives comply with this confidentiality provision as if they were parties to this Agreement and are responsible for any breach of this confidentiality obligation by their Representatives.
- The provisions in this Article will remain valid even after the termination or expiration of this Agreement.
- Pintu will not be liable for any deficiencies, non-performance, errors, interruptions, or delays in fulfilling its obligations in this Program if caused, in whole or in part, directly or indirectly, by events beyond Pintu’s control.
- The Parties agree to waive Article 1266 of the Indonesian Civil Code to the extent that a court decision is required to terminate these Terms and Conditions.
- By participating in the Program, the reporter agrees that the reporter will be bound by Pintu’s Privacy Policy.
- The reporter acknowledges and agrees that they will protect, indemnify, and hold Pintu and its directors, officers, employees, and/or affiliates harmless from and against all claims, losses, liabilities, costs, and expenses that Pintu may incur or suffer or that may be brought against Pintu arising directly or indirectly from or in connection with any failure by the reporter to comply with these Terms and Conditions, Pintu’s terms and conditions, and Pintu’s privacy policy available in the Pintu application and/or in fulfilling their obligations under applicable laws and regulations.
- Without prejudice to the substance of other provisions in these terms and conditions and to the extent permitted by applicable laws, the reporter agrees and understands that Pintu’s liability for any losses or damages arising in connection with the Program is limited to Rp500,000.
- This Program is solely created by PT Pintu Kemana Saja without any cooperation and/or affiliation with any company or organization.