Beware of Crypto Dust! Here’s How “Dust” Attacks Work and Risks in the Cryptocurrency World

Jakarta, Pintu News – Behind the huge opportunities in the world of cryptocurrency (crypto), there are a number of risks and threats that novice investors are often unaware of, one of which is the “crypto dust” attack. The term may sound unfamiliar, but understanding what crypto dust is and how potential dust attacks work can be an important step in keeping your digital assets safe. Don’t let your portfolio be jeopardized just because you let your guard down on this seemingly trivial threat!
What is Crypto Dust? Getting to Know Digital “Dust” in the Crypto World
Crypto dust is a term used to refer to small amounts of crypto coins or tokens that are of minimal value, often too small to trade or move because the transaction fees are greater than the value of the coin itself. Typically, dust appears as leftovers from previous transactions-for example, small fragments of Bitcoin , Ethereum , or Ripple in your wallet.
Many crypto users consider dust unimportant and tend to ignore it. However, this amount of “digital dust” can build up in wallets, and this is where new potential risks arise. Dust can be an opening for cybercriminals to carry out what is known as a dusting attack, where they deliberately send small amounts of crypto to thousands of wallets as part of a cybercriminal action.
Also Read: Cardano (ADA) 2025 Price Prediction: Governance Drama and Investor Fate, What Happened?
How does Dust Attack Work in the Cryptocurrency World?
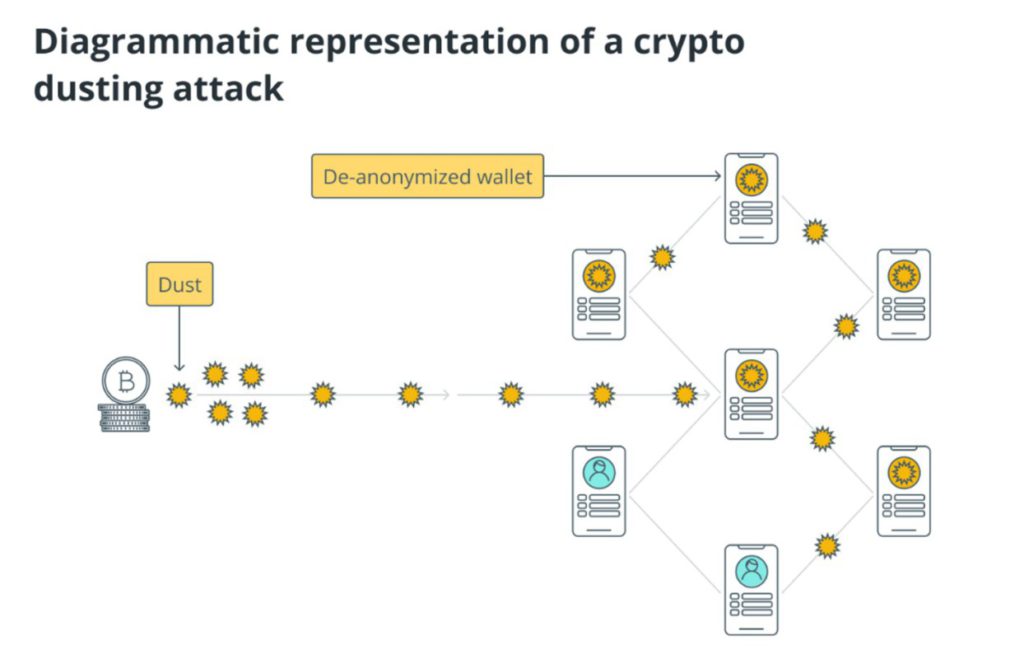
Dust attack is an attack method where the attacker sends crypto dust to many different wallet addresses randomly. The main goal of this attack is not to steal assets directly, but to track the movement and identify the wallet owner based on continued transaction activity. By analyzing how the dust is used or combined with other coins, the perpetrator can uncover the identity of anonymous users on the blockchain network.
The main threat of a dust attack is not just the loss of a small amount of crypto, but the leakage of privacy data. Cybercriminals can link the wallet address to the victim’s real identity, and then proceed with phishing attacks, extortion, or other more dangerous scams. In the crypto world, privacy is everything-and a dust attack can be the start of big problems if not watched out for.
How to Protect Yourself from Crypto Dust and Dust Attack Threats
To prevent the risk of dust attacks, crypto users need to be more vigilant about every small transaction that goes into their wallet. Never mix suspicious dust with your main balance or make compound transactions without analysis. Many modern wallets now provide an “ignore dust” feature or automatic separation of small transactions to increase security.
Always enable layered security such as two-factor authentication (2FA) on your wallet, and monitor wallet activity regularly. If you receive a very small amount of crypto from an unknown source, ignore it or consult the relevant platform support before taking any action. Also, be sure to keep up to date with the latest security information in the cryptocurrency world, as cyberattack techniques are always evolving.
Conclusion
Crypto dust may seem harmless, but it can be an entry point for cyberattacks in the crypto world. Don’t underestimate the “digital dust” that appears in your wallet-protect the privacy and security of digital assets with education, the latest security features, and the discipline of transaction analysis. The world of cryptocurrency is full of opportunities, but prioritize data protection and wallet security to make your investment journey safer and more comfortable.
Also Read: 3 Cryptos to Buy Before Trump’s New Tariffs in August 2025!
That’s the latest information about crypto. Follow us on Google News to get the latest information about the world of crypto and blockchain technology. Check today‘ s bitcoin price, today’s solana price, pepe coin and other crypto asset prices through Pintu Market.
Enjoy an easy and secure crypto trading experience by downloading Pintu crypto app via Google Play Store or App Store now. Also, get a web trading experience with various advanced trading tools such as pro charting, various types of order types, and portfolio tracker only at Pintu Pro.
*Disclaimer
This content aims to enrich readers’ information. Pintu collects this information from various relevant sources and is not influenced by outside parties. Note that an asset’s past performance does not determine its projected future performance. Crypto trading activities are subject to high risk and volatility, always do your own research and use cold hard cash before investing. All activities of buying andselling Bitcoin and other crypto asset investments are the responsibility of the reader.
Reference:
- Exodus. What is crypto dust and how is it used in attacks?. Accessed July 24, 2025.




