What is a Sybil Attack?
While the blockchain world is full of opportunities, it’s essential to remain mindful of potential risks, one of which is the Sybil Attack. This attack allows attackers to steal funds and even take control of a blockchain project by creating multiple fake identities. So, what exactly is a Sybil Attack, and how can you avoid it? Let’s read more about it in this article.
Article Summary
- ☠️ A Sybil attack is an online security breach where attackers create multiple fake identities or “nodes” to take control of a blockchain network to steal funds.
- 🙍♀️ The term “Sybil Attack” comes from the book “Sybil” by Flora Rheta Schreiber, which tells about a woman named Sybil Dorsett who has 16 different personalities.
- 👨💻 A Sybil attack involves an attacker creating many fake identities (Sybil nodes) that masquerade as Honest nodes in the network. They then take control of the network by connecting to Honest nodes and disrupting their operations.
- 🪄 Several strategies to prevent Sybil attacks include high-cost consensus mechanisms, algorithm-based crime detection, and positive reputation systems in the network.
What is a Sybil Attack?

A Sybil attack is an online security breach where attackers create multiple fake identities or “nodes” to take control of a blockchain network to steal funds.
Individuals or groups (attackers) with sufficient resources can easily create multiple fake identities in large numbers. In doing so, they create the illusion that more individuals are supporting their goal than they actually are.
The name of Sybil attack comes from the book “Sybil” by Flora Rheta Schreiber, published in 1973. The book tells about Sybil Dorsett, a woman with personality disorder who has 16 different personalities.
Brian Zill and John R. Douceur introduced the term “Sybil attack” in the computer context in a 2002 paper titled “The Sybil Attack”. In the paper, they explained how attackers could utilize fake identities to take control of peer-to-peer (P2P) networks.
Also, read the Definition of Nodes and their Functions in Blockchain.
How the Sybil Attack Works
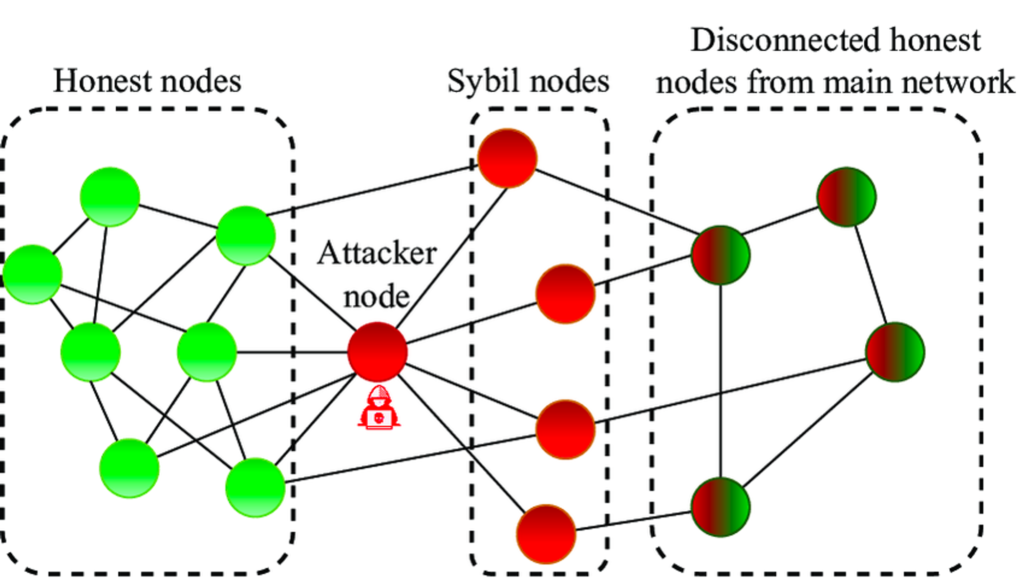
Sybil attack involves three nodes: Honest node, Sybil node, and Attacker node. To execute a Sybil attack, the attacker creates multiple Sybil nodes (as fake identities). The Sybil nodes then masquerade themselves as Honest nodes and trick the Honest nodes to connect to each other.
After successfully connecting with Honest nodes, Sybil nodes then disconnect Honest nodes and take control of the network. Thus, Sybil nodes can control and cause security threats in the network.
On a large scale, Sybil attacks can cause attackers to achieve a more serious level of control over the network, even to the level of controlling the network’s computing power. It is often called a 51% attack because the attacker owns more than 50% of the network’s computing power.
As such, Sybil nodes can then manipulate data, change the order of transactions, and even refuse block creation. It leads to users losing trust in a certain blockchain.
In DAO systems, Sybil attack can manipulate voting results on proposals by controlling multiple identities. In addition, a Sybil attack can also take control of the project's direction by buying most of the governance tokens of a blockchain project. However, it requires a large amount of capital.
Examples of Sybil Attacks
1. Sybil Attack on TOR Network
One of the early Sybil attacks on P2P networks hit the Tor Network in 2014. TOR is a peer-to-peer network that facilitates private conversations.
The attacker conducted a Sybil attack to find the location and identity of Tor users. He controlled around 115 relays from a single IP address. It means that only one individual controlled those many relays. It gave the attacker massive control over the network and access to sensitive information.
2. Sybil Attack on Monero
In 2020, attackers conducted a Sybil attack on the Monero (XMR) cryptocurrency, aiming to breach blockchain data privacy by linking transaction data with IP addresses.
The Monero development team stopped the attack and mitigated most of the damage with Monero’s privacy algorithm. However, some user data information has been leaked.
3. Connext Network Token Airdrop
Sybil attacks can also take place during the token airdrop process, as was the case with Connext Network, a protocol that interfaces with native blockchain bridges. Connext Network encountered a Sybil attack during its native token airdrop, where the attacker generated multiple wallets to qualify for claiming tokens through the airdrop.
A new wallet account was created four hours before the airdrop went live. The wallet was able to claim over 200 tokens for itself through multiple wallets. The airdrop rules only allow one claim per wallet.
The attacker then sold the tokens and profited approximately 38,000 US dollars. In addition, the wallet sent a large spam that took the airdrop user interface offline.
How to Prevent a Sybil Attack

High-Cost Consensus Mechanism
The primary goal in a Sybil attack is to take over the blockchain to steal funds. However, expensive consensus mechanisms can make this endeavor impossible. For example, on Ethereum, a stake of 32 ETH (worth 52,160 US dollars as of September 6, 2023) is required to run a single node. Thus, running multiple nodes for a Sybil attack is extremely expensive.
The PoS consensus algorithm requires node operators to stake a large amount, and if they make a mistake, the system will slash their stake. So, running Sybil nodes would be expensive and complicated.
In addition, an attacker would need to own 51% of the circulating ETH crypto asset supply to take control of the network. The cost of this is extremely high and makes it impossible.
On the other hand, PoW networks like Bitcoin are also challenging to attack because the hardware required to mine BTC is pretty expensive. In other words, the cost of a Sybil attack would be much more expensive than the potential gains.
Algorithm-based Detection
Computer scientists and blockchain developers have designed algorithms to monitor the Sybil nodes in P2P networks. These algorithms can detect unusual or out-of-the-rule actions in network operations.
If these algorithms detect irregularities, they will provide alerts or even automatically activate security systems.
Reputation System
The reputation system is one of the approaches to preventing Sybil attacks. In this system, participants who have been verified and have a positive track record in the network are given greater access rights than new members who have yet to be verified.
Verified participants have a higher level of access or more significant influence in decision-making. This system can later utilize the Soulbound Token (SBT) as a user identity token. SBT can assign voting power based on the user’s interaction and reputation with the community.
Read more about Soulbound Token (SBT) in this article.
Conclusion
Sybil attacks on blue chip crypto assets like Bitcoin and Ethereum have less impact thanks to their high decentralization and strong communities. Nevertheless, all crypto projects should exercise caution regarding potential Sybil attacks, which can result in data breaches and substantial financial losses.
Numerous blockchains are more susceptible to Sybil attacks, which can compromise privacy and security. Consequently, every blockchain network must implement preventive measures to shield themselves from these threats. Employing a combination of preventive actions can enhance overall security.
References
- Cyberscope, What are Sybil Attacks on the Blockchain, Medium, accessed 5 September 2023.
- Fáwọlé John dan Ciattaglia Luciano, Sybil Attack in Blockchain: Examples & Prevention, Hacken, accessed 5 September 2023.
- Worldcoin Team, What is a Sybil Attack? A 101 Guide, Worldcoin, accessed 5 September 2023.
- Xenia Soares, What Is a Sybil Attack? BeInCrypto, accessed 5 September 2023.
Share